2025.12.11更新:
- 高级检测新增了ja4和ja4_r指纹
2025.11.30更新:
- 修复了一些bug
2. 更新了新的检测!适合想要尝试更高难度检测的大佬!
检测网站合集:
1.初级,请求头检测+tls检测:→ https://www.ma2e.top:4443/ ←
2.中级,请求头检测+tls检测+h2检测:→ https://www.ma2e.top:4442/ ←
3.高级,请求头检测+tls检测+h2检测+??:→ https://www.ma2e.top:4445/ ←
注:高级的??检测不太稳定,建议使用edge进行测试
注注:由于刚写完,没有测试太多浏览器和请求库,如果有bug或者误杀正常浏览器,可以在下方留言!
注注注:目前已知360浏览器和QQ浏览器暂不支持
之前没有讲具体的实现方式,我是使用websocket建立tcp链接,手动对tls数据进行解析:
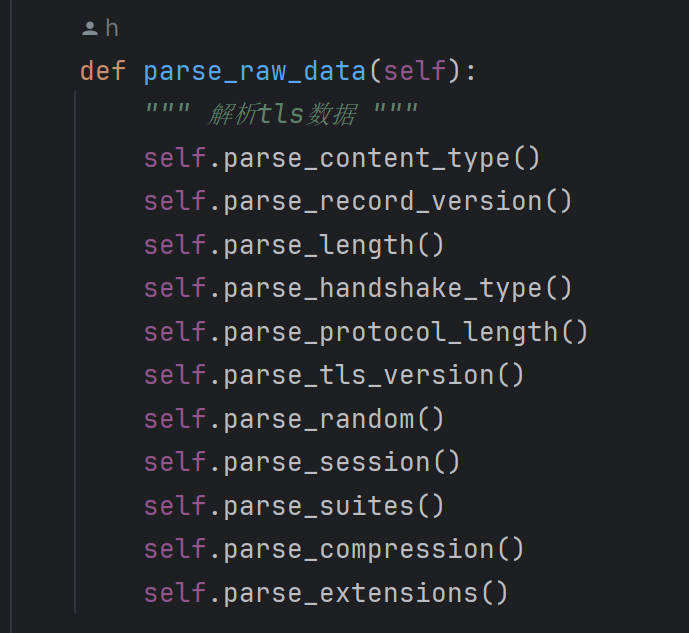
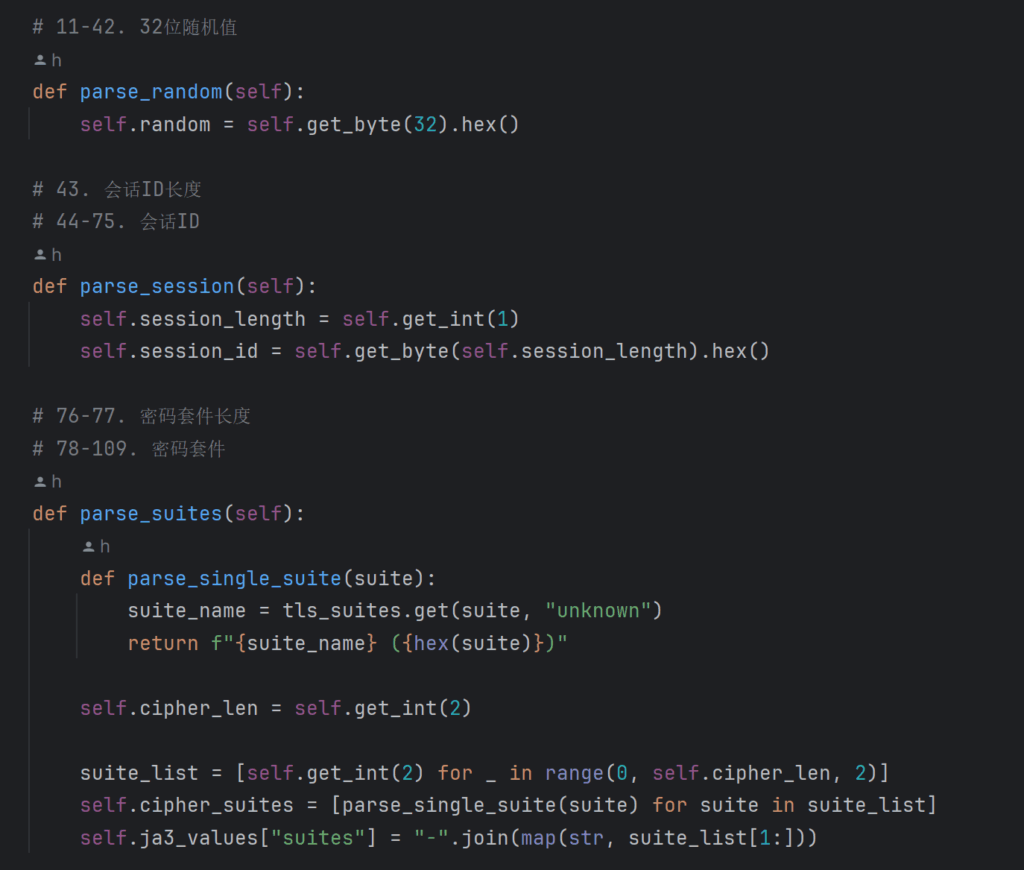
再设置alpn,让他支持http2协议: context.set_alpn_protocols(['h2', 'http/1.1'])
再加上hyper-h2库就可以检测http2的指纹
相较于之前的tls检测,现在的版本加上了http2的解析与检测,生成了对应的akamai_fingerprint
结果类似如下:
{
"http2": {
"akamai_fingerprint": "1:65536;2:0;4:6291456;6:262144|15663105|0|m,a,s,p",
"akamai_fingerprint_hash": "52d84b11737d980aef856699f885ca86"
},
"client_hello": {
"tls_check": true, # 通过这里来判断是否通过了校验
"ja3": "771,4865-4866-4867-49195-49199-49196-49200-52393-52392-49171-49172-156-157-47-53,5-45-10-11-16-13-51-43-17613-23-65281-27-65037-35-18,4588-29-23-24,0",
"ja3_hash": "183888ea2de5bab31cd7dc01e8b5ecd4",
"content_type": "HANDSHAKE",
"record_tls_version": "TLSv1.0",
"tls_length": 1728,
"handshake_type": "CLIENT_HELLO",
"protocol_length": 1724,
"tls_version": "TLSv1.2",
"random": "877faaede596fa641b47c3d4c8e513d39223c9763b2488e9cca2a10a58a6bba6",
"session_length": 32,
"session_id": "2fe4e5dec5707733e9422a8ae9dc6dc4e0ebea1870e52755825ec570a22bd01c",
"cipher_len": 32,
"cipher_suites": [
"GREASE (0x6a6a)",
"TLS_AES_128_GCM_SHA256 (0x1301)",
"TLS_AES_256_GCM_SHA384 (0x1302)",
"TLS_CHACHA20_POLY1305_SHA256 (0x1303)",
"ECDHE-ECDSA-AES128-GCM-SHA256 (0xc02b)",
"ECDHE-RSA-AES128-GCM-SHA256 (0xc02f)",
"ECDHE-ECDSA-AES256-GCM-SHA384 (0xc02c)",
"ECDHE-RSA-AES256-GCM-SHA384 (0xc030)",
"ECDHE-ECDSA-CHACHA20-POLY1305 (0xcca9)",
"ECDHE-RSA-CHACHA20-POLY1305 (0xcca8)",
"ECDHE-RSA-AES128-SHA (0xc013)",
"ECDHE-RSA-AES256-SHA (0xc014)",
"AES128-GCM-SHA256 (0x9c)",
"AES256-GCM-SHA384 (0x9d)",
"AES128-SHA (0x2f)",
"AES256-SHA (0x35)"
],
"compression_method": 1,
"padding": 0,
"extensions_length": 1619,
"extensions": [
{
"name": "GREASE (0x3a3a)",
"length": 0,
"data": ""
},
{
"name": "status_request (0x5)",
"length": 5,
"data": "0100000000"
},
{
"name": "psk_key_exchange_modes (0x2d)",
"length": 2,
"data": "0101"
},
{
"name": "supported_groups (renamed from \"elliptic_curves\") (0xa)",
"length": 12,
"data": [
"GREASE (0xfafa)",
"X25519MLKEM768 (0x11ec)",
"X25519 (0x1d)",
"secp256r1 (0x17)",
"secp384r1 (0x18)"
]
},
{
"name": "ec_point_formats (0xb)",
"length": 2,
"data": "0100"
},
{
"name": "application_layer_protocol_negotiation (0x10)",
"length": 14,
"data": "000c02683208687474702f312e31"
},
{
"name": "signature_algorithms (0xd)",
"length": 18,
"data": "001004030804040105030805050108060601"
},
{
"name": "key_share (0x33)",
"length": 1263,
"data": "04edfafa00010011ec04c0281842a298685b2aa2cb2485118857b2d0bf5b6505461044c9981ed041bc9262325cc258e3c502dfb082d431b7fbf805c7e86632d8a29daabf334179275811bc1170c4647dda601cd359cbcc402b9d47176b1a276d90731b8a32fc45591105762b4953c11434d53b7e7fc191ec1834166aa6e7d2bfb685b023897fe0924545ba480d052cbd9bb255fc0ea9424145154845abc55be76764f651572a787361b0751c237a3654639bba9c24abf0049b231b3596512bb5b3c283fa3213d8608a32579d338783a76c9f086b1328aa27298bfbf94bf51368c7ab56145aa88051b1071b590802c68662998dd4b0d7670a8ff56b61c287e5a0a68587beab706b4ca2085e708f878297c14bc3db913294f21fe11023a0b2907ca12b7ef4042f5a3da4d901583c1a8064afa492ca3dd487f554664028727e0626bfc9c8913a8e66a16bebbc5fc9d532c1c960945244c7193b12065b7ac9c06732047dfb3ee726869c3b0086d52fca08883ccb2edcd24b8441c860fa36987a8483439ff617052e7c572f385dcde7444ec0244e211ef9895c59e19ac9d33f5726a68722aaa549b4a66aabb7b473f6c5636ee097c155ac0c3210a1fac653e278079c4c8bb84003bc811e2ba0eeb99adb41320ebb091347c8ab256a665c1bfe6120d66c2807655653450c5e804a39f63619674d9c4bcb76e769ff556e3ab81ff9e9543ac609a1600c311628b4f25bf976b1a55b4b9979b7b59b0b52c648c03ba4e03818b58970e54c4cd82a0941bcbcf0f68684c1a54889b5e0594f34d84fda9599b2e37642b804e3db6d2b8032541a8e09832496748de3311bb260935e57171f4b486d370964e089f274c3f8fcca6a37abfff336ccda920f1169def5755335102db658c3b759c246bccd300a9ec03d9733bb907c52b16046450ccab942a7ceebad4ccc9798091cd599ca72c53930f89f4cf55d57814a96ec3c861965ced533e2c9c314f52fe08c71f164493bf8bc8f7899483459d0fbbe3db29307695318d8b747cc3030d291e443291a322e1b97c110c1777d9a61f0c57a35152eee64016272438540bb7cc9347c538b17a95a0023b850bc9e661216a43378cf60844c5701507ba2addcab68f37677caa229e58bd934b4ada189ccacb21e90113bc52a3e5358fdcbc7a61acceb188ae612af87568abe1a925b3a7bdb6572d2f81f7121b9b15b70aafa8962584e61f75178500146095ab4396904303a880500f73c9b75f65439b1741d72605df394d7b480eb965cca4859902a8fa825b480a6008a0923da7394c82a92d4ca63dcb53d65b730ab69c8f907ca07c32a9448739981440cc85a2ca47a16915b40177300dc62bef44e35276d19329df69b021965b1a4f7963e6a01ea6a274eeb2481c969f96a1ce0069bb836008e7a9e7f867d59c00ac7e4531599059812068fe3cdde0165ab140a46d4cdc2106597db3ab21321259505156c2c9139749c61cf974401f40120daa37937fc53cd939fb9347100ea1a66938b8bbb2ece65701db06f422717a61c95b2b2024aab8ba7fa4545aa36d6e0255d28389a87b0ddd34c87b769d9b3348131cfa9b014a667b44f91a8d0024520964b8a8a7135eac852a11606e40d272876f69b944d92ea40d2caa815fc70c7712a489afacec4262028ef6d7e6191ca05ab66d54b0610ce7d069b83a9d8cdd398c4189eb6e4649c02fd46fe977589649f437e687d001d0020d785135c9869f6d2fb6e60598ae6ba0275e45c367e35478756d928aa7c987a26"
},
{
"name": "supported_versions (0x2b)",
"length": 7,
"data": "063a3a03040303"
},
{
"name": "application_settings (0x44cd)",
"length": 5,
"data": "0003026832"
},
{
"name": "extended_master_secret (0x17)",
"length": 0,
"data": ""
},
{
"name": "renegotiation_info (0xff01)",
"length": 1,
"data": "00"
},
{
"name": "compress_certificate (0x1b)",
"length": 3,
"data": "020002"
},
{
"name": "encrypted_client_hello (0xfe0d)",
"length": 218,
"data": "00000100010e0020acb15b8ab13f4aaad8dd0634124f1aa5ba59a1183dda967d5e07524c883be26300b00ffffba848848952ba658e3e11ec9b3334f9833c9f96f19d0b16bf2276fd1cbcd8714d99190aba87459101d5d27c9aaee401bc51d28363466baf1f30232f46ceab6449858517a8a73541b1b082e786a6d4bacef1640ca587869f63508506d8f1190697091684a515f765fb250b984b3b98283d9a66e5f13cd78ea52037e946fe3ee9d03a6fa105087f7d870ab2787a78c10e65c997b390e37f062c9cf579ab5dfee8560b915b660902b5a74bd4db3735"
},
{
"name": "session_ticket (renamed from \"SessionTicket TLS\") (0x23)",
"length": 0,
"data": ""
},
{
"name": "signed_certificate_timestamp (0x12)",
"length": 0,
"data": ""
},
{
"name": "GREASE (0x7a7a)",
"length": 1,
"data": "00"
}
],
"curves": [
"GREASE (0xfafa)",
"X25519MLKEM768 (0x11ec)",
"X25519 (0x1d)",
"secp256r1 (0x17)",
"secp384r1 (0x18)"
],
"browser_type": "chrome"
}
}
发表回复